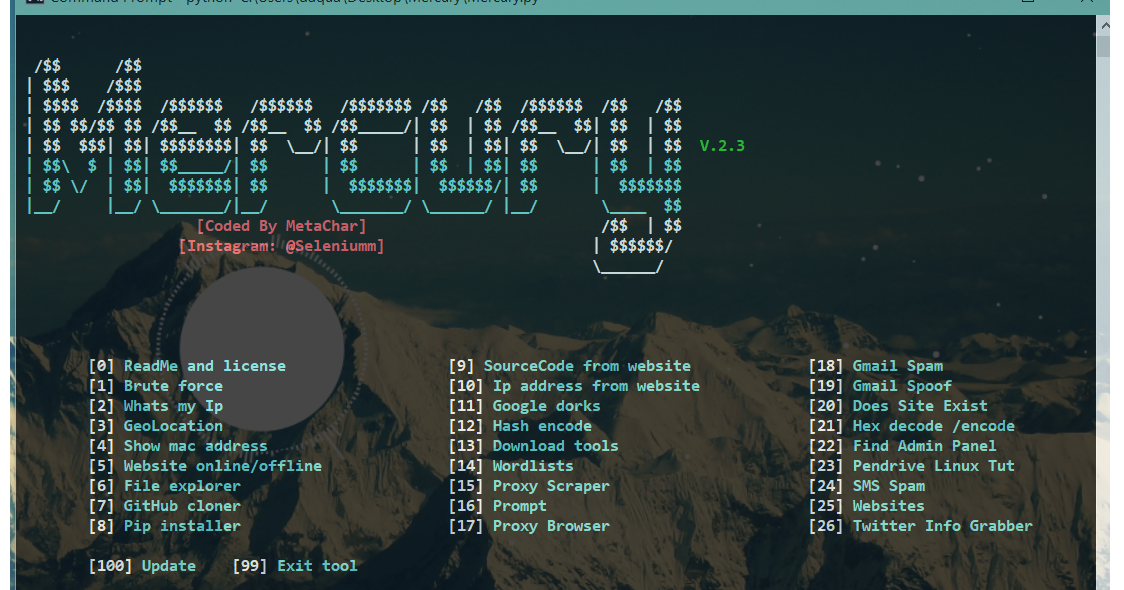
Mercury A Hacking Tool Used To Collect Information And Use The
Mercury is a hacking tool used to collect information and use the information to further hurt the target - 4n6strider/Mercury. Skip to content. Toggle navigation. Sign in Product Actions. Automate any workflow Packages. Host and manage packages Security. Find and fix vulnerabilities.

Как разблокировать телефон, если забыл пароль, пин или графический ключ
Microsoft labels Iranian-affiliated attackers as "Mercury." This group initiated the network access, apparently via Log4j vulnerabilities, and then handed off operations to a "DarkBit persona.

War Robots Galahad Mercury Hawk Leech Test Server Gameplay YouTube
Mercury Security has been informed of a firmware security issue affecting the following hardware: LP1501, LP1502, LP2500, LP4502, and EP4502. This issue makes it possible for a hacker to have a level of access to these controllers. This is done through the Web Browser that accesses and configures Mercury controllers.

THE GREAT HACK DOC NYC
Brunswick Corporation calls itself the global leader in marine recreation and is home to 60 industry-leading brands, including Mercury Marine, which specializes in boat engines and propellers.

AVAKIN Life Hack.pdf DocDroid
The personal information of "potentially" 3.5 million people was compromised by an "international software hack" of Oregon's Department of Motor Vehicles, according to ODOT.

Venly launches MetaRing Membership Your Pass across the Metaverse
Critical Mercury Security Vulnerabilities. HID's Mercury Security has 8 vulnerabilities, including the highest possible 10.0 risk, and researchers recently demonstrated how to hack open a door while using one of the industry's biggest brands. In this report, IPVM examines the vulnerabilities, exposed by researchers from a US cybersecurity firm.

Eavesdroppers can hack 6G frequency with DIY metasurface Trendradars
April 2023 update - Microsoft Threat Intelligence has shifted to a new threat actor naming taxonomy aligned around the theme of weather.MERCURY is now tracked as Mango Sandstorm and DEV-1084 is now tracked as Storm-1084.. To learn more about the new taxonomy represents the origin, unique traits, and impact of threat actors, to get complete mapping of threat actor names, read this blog.
hipster hack scale AMS Confidential
There is a folder mercury_proj and below are the contents of this folder : In the notes.txt file we have two accounts with encrypted passwords, one is webmaster, the other is linuxmaster. We can.
Lost data stock vector. Illustration of computer, personal 1182516
Merkury Innovations Arcade Fun. I'm happy with it, plus it was only $10 and the design being based on the GB Pocket and GB Color throws me back to my childhood. However, I'm wondering if anyone has figured out how to load their own roms onto it. Most of the games are either poorly translated Japanese games, or knockoffs of other well known games.

Cabo de comando Mercury Gen II/ Mercury Americano SOS Marine Comercio
Features BruteForce Mercury uses Selenium to automatically input passwords into a website GeoLocation Gelocation allows the user to pin point the exact location of the ip address Sms Spam Uses gmail to spam sms Spoof Email Sends anonymous emails Check If Website Exists Mercury checks if the website is real Check if Website Is Down Checks if.

Cabo Comando Motor Popa Mercury Mariner 1114 Pés Geração 1 UFLEX
Located in Auckland, Wellington, Hamilton and Melbourne, Mercury IT manages IT services for more than 3000 users and around 200 organisations, according to its website. "While work is underway to understand and respond to this particular incident we have some key messages for individuals, organisations and members of the public in general.

Mercury Hacks YouTube
Accuro is the latest provider to be hit after a string of cyber-attacks that included a hack on central North Island provider Pinnacle Midlands Health Network in October and the earlier ransomware.
War Robots SUPER THANOS Mercury Hack YouTube
The ransomware gang claimed an attack on the NZ-based MSP earlier this month, and now may have launched a supply chain attack. A ransomware attack by cybercrime gang LockBit 3.0 on New Zealand-based managed service provider Mercury IT appears to have led to numerous organisations from NZ appearing on the gang's dark web victim blog.

Safe & Sound TShirt — Mercury Stardust
Here you can download the mentioned files using various methods. We have listed the original source, from the author's page.However, after time these links 'break', for example: either the files are moved, they have reached their maximum bandwidth limit, or, their hosting/domain has expired.

'Former staff' claim abuse by exRep. Hill in Twitter hack house abuse
Once you have injected your raw shim with SH1MMER, go into the Chromebook Recovery Utility, select the settings icon (⚙️), select Use local image, and then select your injected shim.Alternatively, you can also use other flashers such as BalenaEtcher, Rufus, UNetbootin, and etc. This may take up to 10 minutes, depending on the size of your shim and speed of your USB drive.

MACETE PARA LIGAR MOTORZINHO MERCURY!!!HACK TO TURN ON THE MERCURY
April 2023 update - Microsoft Threat Intelligence has shifted to a new threat actor naming taxonomy aligned around the theme of weather.MERCURY is now tracked as Mango Sandstorm.. To learn about how the new taxonomy represents the origin, unique traits, and impact of threat actors, and to get a complete mapping of threat actor names, read this blog: Microsoft shifts to a new threat actor.